SC-300 Microsoft 身份存取和管理員- 02.實行驗證和存取管理解決方案
SC-300:實行驗證和存取管理解決方案
- 使用 Multi-Factor Authentication 保護 Azure Active Directory 使用者
- 管理使用者驗證
- 規劃、實作及管理條件式存取
- 管理 Azure AD Identity Protection
- Password complexity rules
- Password expiration rules
- Self-service password reset(SSPR) - Microsoft 365 Basic
- Azure AD Identity Protection - P2
- Azure AD password protection - 通知不常見位置的登入通知
- Azure AD smart lockout - 依嚴重程度鎖住帳號
- Azure AD Application Proxy
- Single sign-on (SSO)
- Azure AD Connect
- Azure AD MFA & Conditional Access
Always Think Zero Trust 零信任
Always Verify - Least Access Principle - Assume Breach
明確驗證 使用最低許可權的存取權 假設違反
明確驗證
一直根據所有可用的資料點進行驗證和授權。
使用最低許可權的存取權
使用 Just-In-Time 和 Just-ENOUGH-Access (JIT/JEA) 、風險型適應策略和資料保護來限制使用者存取。
假設違反
最小化爆炸弧線和區段存取。驗證端對端加密,並流量分析來取得可見度、推動威脅偵測,並改善防護。
Azure AD MFA
1.Account password 帳戶必須有密碼
2.default 帳戶安全功能有4個至少需要啟用一個
3.additional 帳戶安全功能
Azure AD SSPR
有六個帳戶安全功能 (有一些跟MFA相同)
Authentication factors
something you know: 帳密
something you process: Toke device usb, cell phone…
something you are: 驗證成功
Condition Access
情境 登入風險sign-in Risk
Condition Access policy - Grant - [V] require MFA
情境 使用這有中度風險(登入方式有風險),需要修改密碼
User Risk - high/medium/low/no risk (建議最少勾選Medium)
Condition Access policy - Conditions - [V] require password change
MFA
預設網域>Security>MFA
驗證方法
[]電話通話
[]電話簡訊
[]行動應用程式的通知
[]來自行動應用程式或硬體Token的驗證碼
Use the search feature and search for multi-factor.
On the Getting started page, under Configure, select Additional cloud-based MFA settings
set up Conditional Access policy rules that would enforce MFA for users accessing specific apps on your network
select Azure Active Directory > Security > Conditional access.
Users or workload identities
Cloud apps or actions
Locations
Access Controls - Grant
Enable policy to On
Configure Azure AD Per-User MFA
At the top of the Users pane, select Per-user MFA.
You can enable or disable MFA on a user basis by selecting a user and then using the quick steps on the right side.
Read the notification popup if you get it, then select enable multi-factor auth button.
SSPR (Self service password reset)
Azure Active Directory blade.
Under Manage, select Password reset.
On the Password reset blade Properties page, under Self service password reset enabled, select Selected.
Select Select group.
In the Default password reset policy pane, select the SSPRTesters group.
On the Password reset blade Properties page, select Save.
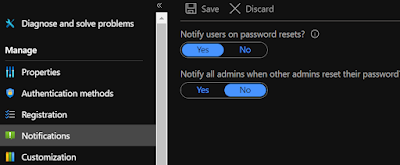
Under Manage, select and review the default values for the Authentication methods, Registration, Notifications, and Customization settings.
Authentication methods
Registration
Notifications
Customization
register a mobile phone number
https://aka.ms/ssprsetup
Open a different browser or open an InPrivate or Incognito browser session and then browse to https://portal.azure.com.
Enter yourAzureAD_UserAccount@ <<organization-domain-name>>.onmicrosoft.com and then select Next.
Note - Replace the organization-domain-name with your domain name.
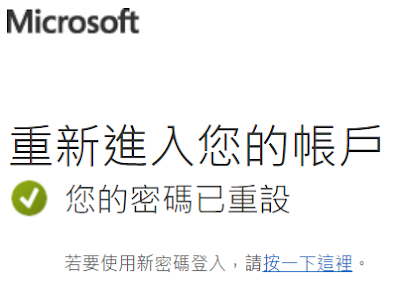
On the Enter password page, select Forgot my password.
What happens if you try a user not in SSPRTesters group?
As a test, open a new InPrivate browser window and try to log into the Azure Portal as GradyA, and select Forgot my password option.
Lab 14 - Working with security defaults
Organizations that choose to implement Conditional Access policies that replace security defaults must disable security defaults.
組織實作Contitional Access Policy必須先停安全性用預設值
Lab 15 - Implement and test a conditional access policy
Verify you are prevented from successfully access Azure Portal.
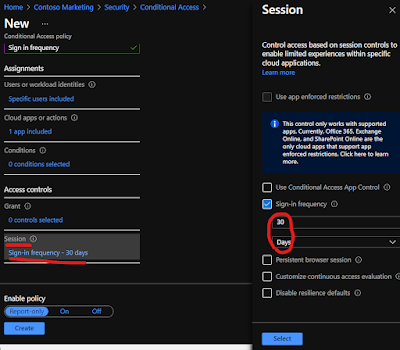
Lab 16 - Configure authentication session controls
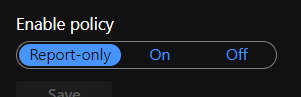
- Conditional Access policies can be enabled in report-only mode.
- During sign-in, policies in report-only mode are evaluated but not enforced.
- Results are logged in the Conditional Access and Report-only tabs of the Sign-in log details.
- Customers with an Azure Monitor subscription can monitor the impact of their Conditional Access policies using the Conditional Access insights workbook.
Lab 17 - Manage Azure AD smart lockout values
In the Password protection settings, in the Lockout duration in seconds box, set the value to 120.
Next to Mode, select Enforced.
NOTE - When the smart lockout threshold is triggered, you will get the following message while the account is locked:
Your account is temporarily locked to prevent unauthorized use. Try again later, and if you still have trouble, contact your admin.
使用 Azure Active Directory 智慧鎖定防止使用者帳戶遭受攻擊
https://docs.microsoft.com/zh-tw/azure/active-directory/authentication/howto-password-smart-lockout
根據預設,智慧鎖定會在10次失敗的 Azure 公用和 Azure 中國的世紀租使用者嘗試10次失敗之後,將帳戶從登入嘗試鎖定一分鐘,且 Azure 美國政府租使用者為3。 在每次後續登入嘗試失敗之後,帳戶會再次鎖定,先鎖定一分鐘,後續嘗試鎖定時間會更長。 為了將攻擊者規避此行為的可能性降至最低,我們不會公開其他失敗登入嘗試的鎖定期間增加速度。
智慧鎖定會追蹤最後三個不正確的密碼雜湊,以避免因為相同密碼而累計鎖定計數器。 如果有人多次輸入相同的錯誤密碼,此行為不會造成帳戶鎖定。
Azure Identity protection (Azure IP)
風險偵測
針對有異常登入使用者,所需要採取的回應動作
Lab 18 - Enable sign in and user risk policies
Azure Active Directory > Security > Identity protection > User risk policy.
Conditional Access可以控制那些使用者或條件必須使用MFA
Azure Identity protection則是針對有異常登入使用者,跳出必須啟用MFA
Lab 19 - Configure an Azure AD multi-factor authentication registration policy
Under Controls, notice that the Require Azure AD MFA registration is selected and cannot be changed.
Under Enforce Policy, select On and then select Save.
















































沒有留言:
張貼留言